As nations work towards a more resilient and digitally sovereign future, the pursuit of cloud sovereignty has emerged as a critical imperative for governments globally. Gartner forecasts that over 50 countries will be engaged in domestic sovereign cloud initiatives by 2026, reflecting a collective effort to assert independence, autonomy, and decision-making authority in the cloud.
Many would have noticed Microsoft’s announcement last week regarding the general availability of Microsoft Cloud for Sovereignty across all Azure regions. Promoted as an avenue to open “new pathways for government innovation,” Microsoft will provide multiple sovereign landing zones tailored for organizations seeking to leverage economies of scale to accelerate cloud-based innovation while addressing compliance and privacy concerns. However, to fully capitalize on the advantages of hyperscale sovereign cloud, customers must utilize the Azure ecosystem and adhere to Azure guidelines for national and regional regulatory compliance. With this level of lock-in, do these initiatives genuinely contribute to digital sovereignty? Or are these sovereign cloud regions merely tools for managing compliance?
What is digital sovereignty?
Globally there are concerns over the influence of foreign technology companies in the cloud, which threatens control over personal data and constrains both the growth of local advanced technology companies and the ability to enforce national laws.
In this context, ‘digital sovereignty’ refers to the ability to act independently in the digital world.
It should be understood in terms of both protective mechanisms, such as prioritizing local manufacturing and development, and proactive tools to foster digital innovation, resilience, leadership and strategic autonomy in the digital field.
Global dependencies and critical challenges
Excluding the United States and China, all nations face a significant challenge in the context of sovereign clouds: escalating dependencies on a restricted group of countries and providers for hardware and cloud services. Owing to the evolution of the global IT industry over the past few decades, sovereign clouds must be constructed and managed using a very limited number of vendors throughout the entire value chain. Even if you’re contracting an American service provider, hardware is almost exclusively manufactured in China, resulting in a complex and fragmented market with restricted accountability and transparency.
Check-box sovereignty
While the industry has a general consensus on the requirements for cloud sovereignty, it may not always translate into a more digitally resilient future or the best outcome for the customer. The lack of an industry-wide standard for defining a sovereign cloud poses a challenge. For instance, a sovereign cloud built on VMware must adhere to VMware’s specified requirements, which might differ from those of Oracle or Microsoft. Establishing a sovereign cloud often resembles executing a recipe: foreign technology providers outline the steps to be followed, and the system integrator implements them.
This approach might suffice in certain cases; however, for nations seeking greater digital sovereignty, blindly adhering to a set of rules will not yield genuine independence and is more likely to result in vendor lock-in.
This is because these frameworks tend to focus primarily on data and operational sovereignty, neglecting the broader motivations for achieving cloud sovereignty in the first place. While these frameworks serve as a starting point for establishing processes, policies, and administrative activities, they are not the ultimate destination in the pursuit of true cloud sovereignty.
The need for a holistic approach to true cloud sovereignty
True cloud sovereignty embodies a strategic understanding of the motivations that drive the pursuit of digital sovereignty in the first place.
The focus here lies in the notion that the goal of attaining cloud sovereignty goes beyond mere data and personnel isolation within national borders for privacy and control. Rather, it aims to cultivate national resilience to confront the challenges of the future and establish strategic autonomy in the digital realm. This is why key strategies, such as bolstering supply chains, even with trusted partners, fostering local manufacturing, and nurturing skills and capacity development, are fundamental pillars of true cloud sovereignty.
In pursuit of true cloud sovereignty, we introduce a nuanced taxonomy that surpasses conventional ‘check-box’ sovereignty, capturing the dynamic interplay of motivations and strategies for pursuing digital sovereignty. In an unpredictable world, true cloud sovereignty embodies autonomy and resilience, empowering nations to act decisively, safeguard their own data, and chart their own course towards digital sovereignty.
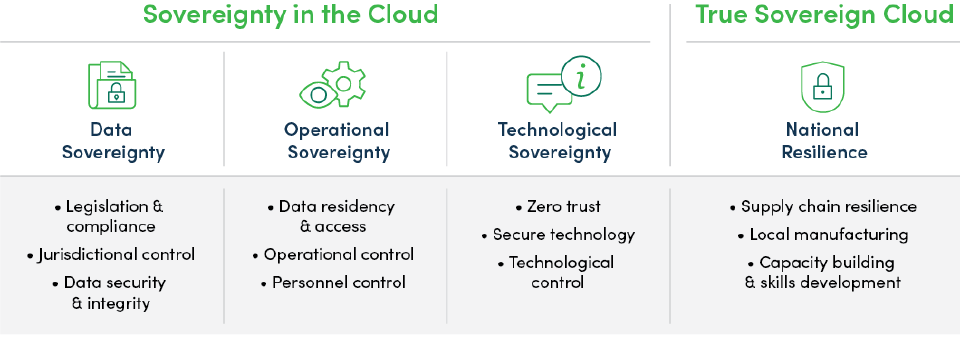
Check-box sovereign cloud
Check-box sovereign is about ticking all the boxes around compliance, control, security and access. It’s the crucial first step in asserting sovereignty in the cloud but it’s not the final destination.
1. Data Sovereignty
Legislation and Compliance
Check-box sovereign clouds adhere to and comply with local legislative and governance frameworks that regulate the access to and handling of data. This involves asserting control over data handling within the nation’s borders. Data privacy is often the primary goal.
Jurisdictional Control
Check-box sovereign clouds establish legal safeguards to protect against extraterritorial laws that may compromise data sovereignty, such as the U.S. CLOUD Act.
Data Security and Integrity
Check-box sovereign clouds implement robust measures where appropriate to ensure the security and integrity of data within the sovereign cloud environment. This may include building for a range of network conditions, including denied, disrupted, intermittent or disconnected environments.
2. Operational Sovereignty
Data Residency and Access
Check-box sovereign clouds emphasize the importance of data residency and controlled access, ensuring that data stays within local territories and is accessible in alignment with operational requirements.
Operational Control
Check-box sovereign clouds assert control over the operational aspects of the cloud, including ensuring management, processes, and procedures, including audit and reporting, happen on-shore.
Personnel Control
Check-box sovereign clouds maintain vigilance over personnel access, ensuring that operational teams are controlled, vetted, and adhere to security protocols.
3. Technological Sovereignty
Zero Trust
Check-box sovereign clouds embrace a ‘zero trust’ approach to security, ensuring that trust is never assumed but continuously verified in all technological interactions.
Secure Technology
Check-box sovereign clouds implement secure and trusted technologies and controls, such as encryption. They also establish continuous monitoring mechanisms to identify and address potential vulnerabilities or disruptions.
Technological independence
Check-box sovereign clouds exercise control over the technological infrastructure reducing dependency on foreign technologies and services where possible.
True Sovereign Cloud
True cloud sovereignty fosters national resilience in the digital realm by cultivating innovation, leadership, and strategic autonomy in the cloud. Achieving true cloud sovereignty enhances cloud independence by reducing reliance on foreign providers and technologies, thereby diminishing vulnerability to disruptions in global supply chains and vendor lock-in.
1. National Resilience
Supply Chain Resilience
True sovereign clouds prioritize localized operations, reducing dependencies on foreign infrastructure and enhancing supply chain resilience. Diversified supply chains with trusted partners further mitigate undue influence by any single company or organization.
Local Manufacturing and development
True sovereign clouds engage local manufacturing of hardware and software development to reduce dependency on foreign suppliers and foster innovation. This enables enhanced capabilities and rapid adaptation to evolving technological landscapes.
Capacity building and skills development
True sovereign clouds develop a highly skilled workforce to build sovereign industry capabilities and play a crucial role in delivering economic growth, and strengthening national security.
Embarking on sovereign cloud initiatives shouldn’t be just about protecting and isolating your data and workloads or leveraging the economies of scale; it should be about orchestrating independence across the entire digital landscape, fostering lasting digital sovereignty.
If you are looking for more independence in the way you build your sovereign cloud, HyperCloud is a new technology that has dramatically lowered the barriers to operating your own private cloud for sensitive data, while also reducing dependence on foreign suppliers and technology.
If you want to learn more about HyperCloud and whether it is right for your sovereign cloud deployment, please get in touch at natsec@softiron.com.






