SoftIron is proud to have received U.S. patent number 11,321,203 “Merged infrastructure for manufacturing and lifecycle management of both hardware and software”. This encompasses the novel baseboard management controller (BMC) SoftIron has pioneered as a key component of modular server architecture.
A baseboard management controller (BMC) is a specialized service processor that monitors the physical state of a computer, network server or other hardware device using sensors and communicating with the system administrator through an independent connection. The BMC is part of the Intelligent Platform Management Interface (IPMI) and is usually contained in the motherboard or other main circuit board of the device to be monitored. It normally monitors environmental variables e.g. temperature, humidity, power-supply voltage, fan speeds, communications parameters and operating system (OS) functions, sending alerts if anomalies are detected.
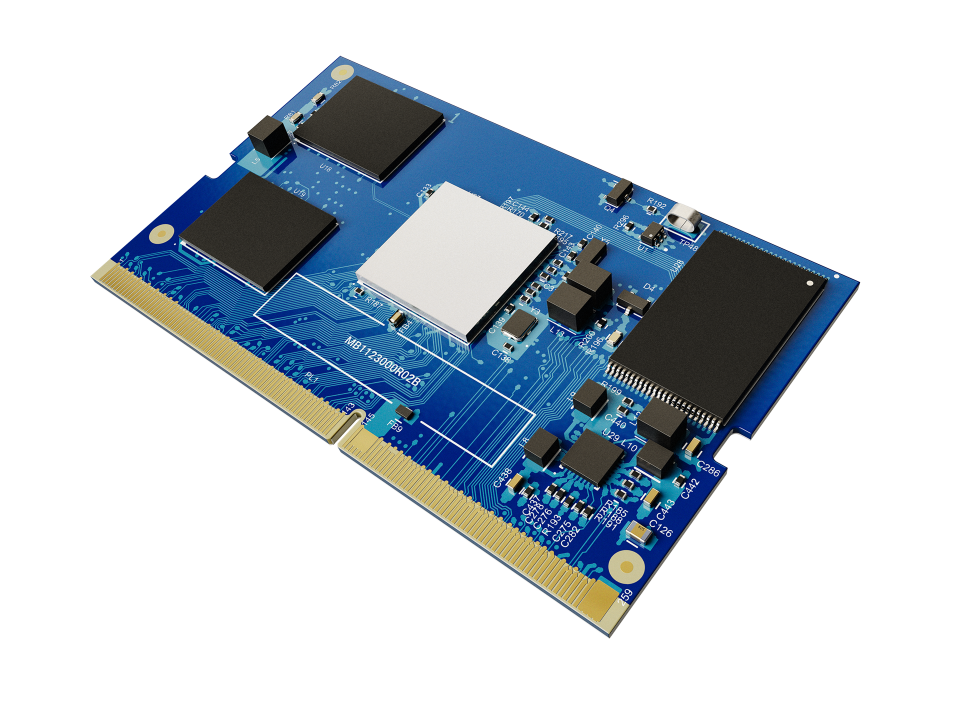
Typically, a motherboard is made by one manufacturer, while the BMC hardware is made by a different manufacturer and the BMC software is written by a provider other than the maker of the motherboard or BMC. As a result, most often a BMC is a generic hardware device (e.g., an ARM-based system on a chip or “SoC”) that is configured relatively statically prior to being installed on a motherboard. This creates a component with limited functionality that is not specifically customized to the particular end system.
By abandoning the generic model, SoftIron, with its patented technology, can augment the BMC functionality and provide some distinct advantages
Unlike most other IT vendors today, SoftIron solely designs and manufactures its own products from component level up, in-house. This results in a modular hardware and software architecture providing freedom to balance functionality, performance and value depending on customer requirements and usage models. The BMC is a foundational element that underpins this approach. Using SoftIron patented system architecture design, the BMC can passively determine the various modules, including the motherboard, which comprise the complete system and create an initial device tree. From that point the entire “footprint” of the system configuration is known, enabling the BMC to complete initial and subsequent programming for the entire product. With a superset of device drivers and the ability to access the main driver memory, the BMC can use the footprint to dynamically configure the device driver set prior to main processor activation.
There are two distinct advantages of this approach. First the BMC is configured to discover the hardware directly. Since the hardware and associated identifiers are manufactured directly by SoftIron, this can act as a provenance check for the discovered configuration. Any anomalous hardware that is not recognized can be isolated. Drivers can be independently re-loaded if a discrepancy is found. Second, the BMC can dynamically adjust to new configurations. Once a new module is identified, the server configuration can be reconfigured to accommodate it during the power on sequence.
Uniquely designed and manufactured by SoftIron, the BMC has a lot more functionality than its off the shelf counterparts. Whether in the field, in soak test, or during initial manufacturing, an assembled product can be put through quality assurance procedures that provide either assurance or audit. These tests can be determined by the discovered system footprint. Under certain circumstances, the BMC may even mimic missing modules by providing phantom drivers to the main system processor. This will also allow the BMC to conduct periodic system assurance tests after the product has been delivered. Not only will this detect system errors, it will verify the system provenance by identifying SoftIron provided hardware and maintain configuration security while providing complete flexibility in customer solutions.
Maintaining device driver code integrity is a common challenge with modular systems. This can be compromised accidentally by adding an incorrect module or malevolently to take over server functions. The BMC is in an exclusive position to rectify both of these situations. As mentioned earlier, the BMC contains a reference copy of hardware drivers. These can be associated with the modules it discovers. The BMC can detect an incorrect module and adjust the server to compensate for it. This may include changing other existing drivers, altering power supplies or temporarily simulating missing modules. During normal operation, the BMC can also independently certify the main processor drivers. Further the BMC can take corrective action such as overwriting corrupted drivers or even halt the system processing. The BMC can send alerts, both locally in the form of server displays, or remotely via the management interface if there is a discrepancy.
The BMC is a complete and separate processing system in parallel to the main system processor. As such it can execute its own set of programming. This can include storing results from any tests performed during overall system operation. These stored results can be highly valuable when an attempted system compromise is detected. In addition to monitoring standard BMC functions, the SoftIron solution can record other server functions. This can become very important if main processing functions become unstable or non-responsive. An administrator can independently connect to the BMC to run diagnostic tests or collect specific server performance data. The latter is enhanced by the ability of the main processor and the BMC to share a common memory space for OS performance logs. Plus the BMC can be instructed to overwrite or reload main processor firmware to aid in a recovery effort. This can be especially valuable in the case of a malicious attack upon the server.
By departing from a standard BMC function and manufacturing all hardware components, SoftIron can provide assurance levels to a very high standard throughout the complete lifecycle of its products. This allows the continuous self certification of provenance of all system components. The BMC can adjust main system firmware to adapt to new system configurations or thwart malevolent attackers. Not only does this produce a wider range of secure products it also future proofs customer hardware by seamlessly accommodating system upgrades.
Learn more about SoftIron’s provenance initiative or task specific design.